KUALA LUMPUR – Ransomhub, the hacker group claiming responsibility for a cyber attack against public transportation provider Prasarana Holdings Bhd, may be operating from Russia with a global network of affiliates.
Using an Onion browser, Scoop identified a website claiming to be operated by Ransomhub which displayed a ransom note for their attack on Prasarana.
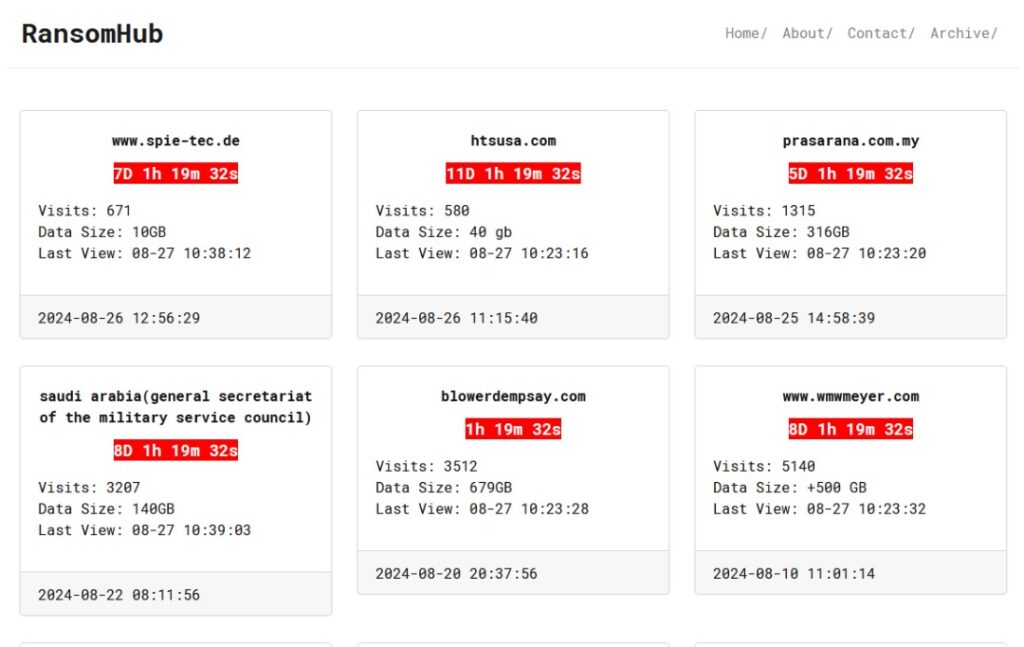
As of the time of writing, Ransomhub’s countdown shows Prasarana has 5 days 3 hours and 37 minutes to pay a ransom, or the hackers would publish 300GB of the company’s files on the public domain. Currently, it is understood that Prasarana has no access to the files.
At the moment, Ransomhub has six live ransom notices including one against the General Secretariat of the Military Service Council of Saudi Arabia, which has 140GB of data compromised.
According to Ransomhub’s About page, the group comprises hackers from various nations who are financially motivated and are prohibited from targeting Cuba, China, North Korea and Commonwealth of Independent States (CIS) countries.

CIS states include Belarus, Russia, Kazakhstan, Moldova, Armenia, Azerbaijan, Tajikistan, Kyrgyzstan, Uzbekistan and Turkmenistan.
However, given the list of countries that Ransomhub refuses to attack, cybersecurity firm Fortra believes that the main administration of the group may be located in Russia or a Russian-friendly nation.
Additionally, Ransomhub says that the group does not allow second attacks on companies or entities that have made payments.
They also claim not to attack non-profit hospitals and certain non-profit organisations.
Ransomhub also says that affiliates who use their ransomware to attack companies must comply with agreements reached during negotiations with targeted companies. Failure to do so will result in Ransomhub’s refusal to work with that group again.
“If the affiliate refuses to send you the decryptor after your payment, you can contact us and we will send you the decryptor for free.
“If a second attack occurs after payment, please let us know and we will provide you with the decryptor immediately,” the About page says.
Scoop contacted Ransomhub and questioned the group on the type of files obtained and the ransom amount demanded from Prasarana.
However, Ransomhub, through a chat with Scoop, refused to reveal details until the countdown is over.

From Lockbit to Ransomhub
The chat ID of Ransomhub’s “spokesperson” appears to be Dmitry Yuryevich Khoroshev, whose name appears in a US State Department notice.
While it is uncertain that the individual in the chat is indeed the wanted individual, Khoroshev is understood to be a Russian national believed to be the administrator of Lockbit, another cybercriminal group that performs ransomware attacks.
However, in previous interviews with various tech news portals, Lockbit says US authorities identified the wrong individual.
Currently, US authorities have placed a US$10 million bounty for information that would lead to Khoroshev’s capture.
According to Fortra, Europol led a crackdown against Lockbit’s servers in February, forcing some of their hackers to switch to Ransomhub’s platform instead.
Meanwhile, Fortra also suggests that Ransomhub’s ransomware is possibly an evolution of a previous malicious tool called Knight.
Ransomware-as-a-service
Basically, Ransomhub operates a ransomware-as-a-service (RaaS) platform, where affiliates gain access to malicious tools to perform hacks.
With the ransomware in hand, hackers attempt to gain access to a company or entity’s network possibly through a phishing email or other means.
Once a network has been successfully infiltrated, the company would not be able to access compromised files unless they pay a ransom to the hackers.
According to https://socradar.io, a cyber threat monitoring and warning site, affiliates of Ransomhub keep a large chunk of the ransom while Ransomhub, which provides the ransomware, gets a smaller percentage of the money.
Further, it appears Prasarana was not the only Malaysian entity to fall victim to Ransomhub as the group also claimed an attack against website kovra.com.my, which makes customised jerseys.
Yesterday, Prasarana confirmed that the company fell victim to a cybersecurity attack involving unauthorised access to part of the public transport operator’s internal system.
In a statement, Prasarana said their cybersecurity team had identified the attack and was currently handling the situation.
So far, Prasarana said the attack has not affected day-to-day operations. – August 28, 2024


